24x7 Cyber Security
Powered by Experts
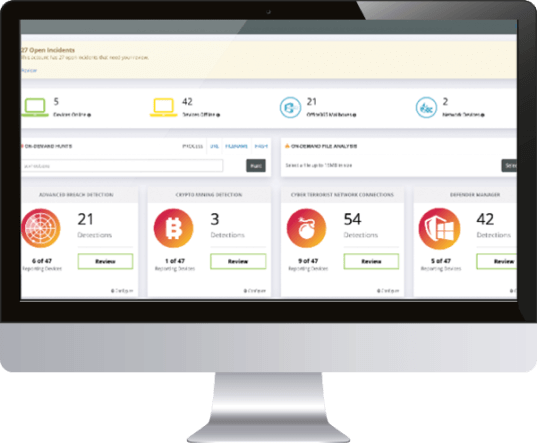
Managed SOC (security opera on center) is a white labeled managed service that leverages the our Threat Monitoring Platform to detect malicious and suspicious activity across three critical attack vectors: Endpoint | Network | Cloud. Our elite team of security veterans hunt, triage and work with your team when actionable threats are discovered including:
Continuous Monitoring
Around the clock protection with real-time threat detection
World Class Security Stack
100% purpose-built platform backed by over 50 years of security experience
Breach Detection
The most advanced detection with to catch attacks that evade traditional defenses
Threat Hunting
Elite security team proactively hunt for malicious activity
No Hardware Required
Patent pending cloud-based technology eliminates the need for on-prem hardware
Managed SOC Key Features
The most comprehensive set of features means you can focus you’re your business while our team of security experts ensures the you have the most advanced protect on leveraging your existing tools and technologies across endpoint, network and cloud.

SIEMLESS LOG MONITORING
Monitor, search, alert and report on the 3 attack pillars: network, cloud and endpoint log data spanning Windows and macOS, Firewalls and Network Devices, Microsoft 365 & Azure AD without requiring SIEM hardware.

THREAT INTELLIGENCE & Hunting
Real-time threat intelligence monitor-ing, connecting to premium intel feed partners giving our customers the largest global repository of threat indicators for our SOC analysts to hunt down attackers.

BREACH DETECTION
Detect adversaries that evade traditional cyber defenses such as Firewalls and AV. Identifies attacker TTPs and aligns with Mitre Attack, producing a forensic timeline of chronological events to deter the intruder before a breach occurs.

INTRUSION MONITORING
Real-time monitoring of malicious and suspicious activity, identifying indicators such as connections to terrorist nations, unauthorized TCP/UDP services, backdoor connections to C2 servers, lateral movements and privilege escalation.

NEXTGEN MALWARE
Use your own malware prevention or leverage our command and control app for Microsoft Defender backed up with a secondary line of defense using our malicious detection of files, tools, processes and more.

PSA TICKETING
Our SOC analysts investigate each alert, triaging the data and produce a ticket to your PSA system accompanied with the remedy details so you can focus on your operations without hiring security additional engineers.
Security App Store
Get more by monitoring your existing tools 24/7 and with our App Store turn on just the monitoring you want with over 35 cybersecurity Apps across the most popular products including:
AV/AM Monitoring with SentinelOne, Cylance, Webroot, BitDefender, Windows Defender, Sophos and Deep Instinct.
Firewall Analyzer & Monitoring with Fortinet, WatchGuard, SonicWall, Sophus, Barracuda, Juniper, Cisco Meraki, PfSense, Untangle, and Ubiqui.
Email Monitoring & DNS Monitoring with Microsoft 365, IRONSCALES, Barracuda, DNSFilter and Cisco Umbrella.
And much more…

With the right level of support for your IoT systems, you can set your home up for the future and beyond. That’s what we’re here for. Getting started is the easiest part.
Getting started is easy. Give us a call at 855-736-3395 or fill out the form below. One of our representatives will touch base and schedule an introductory phone call.
FAQ
Periodic hardware failures and new or updated software are common. Although not considered maintenance, we include handling these situations alongside general maintenance, and they are included in our services.
It's important that you report any issues as soon as possible so we can help resolve them. You can either report them yourself or have your employees reach out to us directly. Either way, we'll be able to help resolve the issue quickly and efficiently. You'll never have to worry about hidden fees or unexpected charges with us.
We pride ourselves on providing excellent customer service. When you call us, you can expect a rapid, courteous response from a real person. We understand how important it is to be able to speak to someone directly when you have questions or concerns, and we will do everything we can to address your needs.
Our IT staff is also certified in a variety of industry-leading technologies. This allows us to offer our clients a wide range of services and support. We are committed to providing our clients with the best possible service and support.
As a leading provider of proactive cybersecurity solutions, we are committed to helping our clients stay one step ahead of the latest threats. Our comprehensive monitoring and detection capabilities provide early warning of potential attacks, allowing our clients to take preventive action before it is too late.
In addition to our proactive monitoring solutions, we also offer a full range of vulnerability scans, intrusion detection, and network security services. Our team of security experts are constantly monitoring the latest threats and developments in the cybersecurity landscape, so you can be confident that your business is always protected.